Secure file permissions: Difference between revisions
No edit summary |
No edit summary |
||
| Line 5: | Line 5: | ||
* Homedirectory: See [[#Homedirectory permissions | homedirectory]] | * Homedirectory: See [[#Homedirectory permissions | homedirectory]] | ||
* www directory (and other directories from where websites are served), including subdirectories: <code>0705/drwx---r-x</code> | * www directory (and other directories from where websites are served), including subdirectories: <code>0705/drwx---r-x</code> | ||
* | * Static website files (css, images, html, ...): <code>0604/-rw----r--</code> | ||
* Configuration files containing secrets/passwords: <code>0600/-rw-------</code> | * Configuration files containing secrets/passwords: <code>0600/-rw-------</code> | ||
* Other directories and files that are not part of a website: <code>0600/-rw-------</code> or <code>0700/-rwx------</code> | * Other directories and files that are not part of a website: <code>0600/-rw-------</code> or <code>0700/-rwx------</code> | ||
Revision as of 17:56, 16 March 2020
PHP code is run with PHP-FPM as your ULYSSIS user. This means you can tighten up you website's security by denying other users the permission to read your PHP files. However, due to the way the Apache webserver works, it must be able to determine the existence of your PHP files. Non-PHP files in your www directory must remain readable by other users, because Apache reads these as it's own user.
Recommended permissions
- Homedirectory: See homedirectory
- www directory (and other directories from where websites are served), including subdirectories:
0705/drwx---r-x - Static website files (css, images, html, ...):
0604/-rw----r-- - Configuration files containing secrets/passwords:
0600/-rw------- - Other directories and files that are not part of a website:
0600/-rw-------or0700/-rwx------
Securing database login info
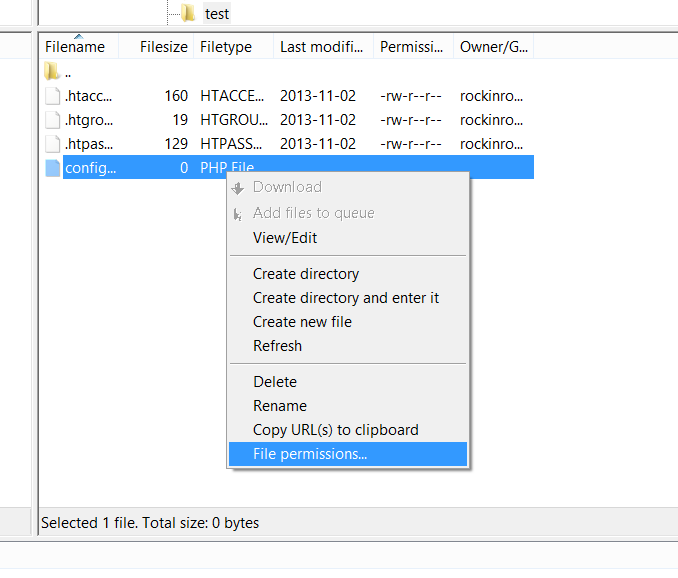
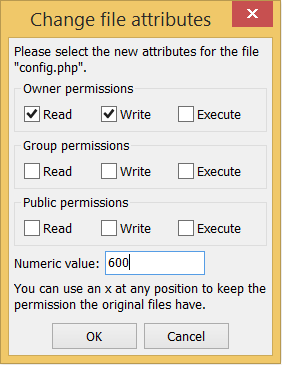
Suppose you have a file called config.php, containing login information for your database. To secure this information, you can make it readable and writeable by only you, and nobody else using chmod 600 config.php. In FileZilla, you can do this by right-clicking on the config file, clicking on "File permissions...", and changing the permissions according to the following screenshots:
Securing uploads directory
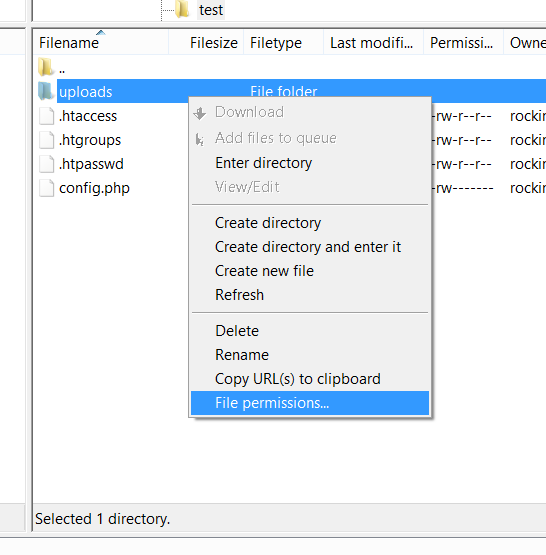
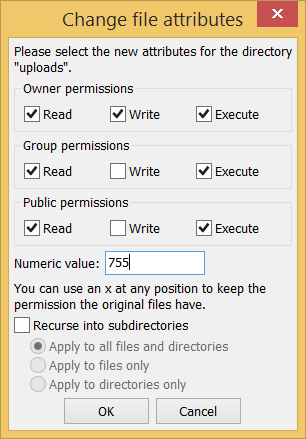
Also, if there are directories that you made writeable by others, e.g. an uploads folder, this is no longer necessary. If this directory is called uploads, you can remove write rights for others with chmod go-w uploads. In FileZilla, you can do this by right-clicking on the config file, clicking on "File permissions...", and changing the permissions according to the following screenshots:
Homedirectory permissions
In order to prevent other users entirely from accessing files in your homedirectory, the permissions on your homedirectory should only allow yourself and the www-data user access. This is by default configured properly for you from the 29th of July, 2018 onward. Note that you should still follow the guidelines as detailed above. If you have changed your permissions on your homedirectory and want to restore the defaults, you can execute nfs4_setfacl -S /home/user/acl ~. The file /home/user/acl contains the default permissions.